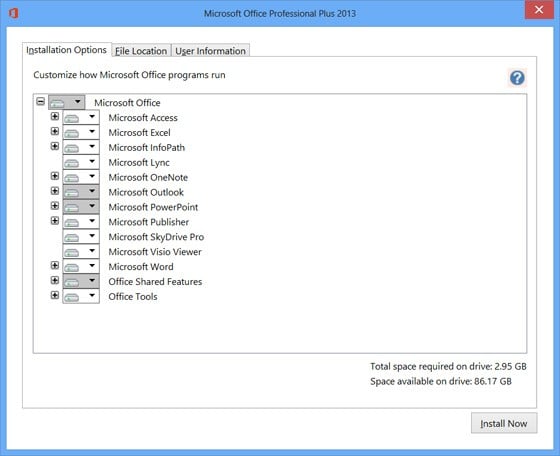
 MS Outlook 2010 Professional Plus Word couldnt send mail because of a MAPI failure Operation not supported. Describes that an Office Professional Plus 2010 user receives an Unlicensed Product message and many features are disabled in Office Professional Plus. Find great deals for Microsoft Office 2013 Professional Plus 32bit 64bit for Windows. Shop with confidence on eBay Download Microsoft Office Starter 2010. Office Starter is not trial software you can continue to use it as long as you need. It just has limited funcionality.
MS Outlook 2010 Professional Plus Word couldnt send mail because of a MAPI failure Operation not supported. Describes that an Office Professional Plus 2010 user receives an Unlicensed Product message and many features are disabled in Office Professional Plus. Find great deals for Microsoft Office 2013 Professional Plus 32bit 64bit for Windows. Shop with confidence on eBay Download Microsoft Office Starter 2010. Office Starter is not trial software you can continue to use it as long as you need. It just has limited funcionality.  Microsoft Office 2. Professional Plus 3. Windows. Operating Systems. Microsoft Windows 1. Microsoft Windows 7, Microsoft Windows 8, Microsoft Windows 8. Microsoft Windows Server 2. Microsoft Windows 1. Microsoft Windows 7 6. Microsoft Windows 8 6. Microsoft Windows 8. Microsoft Windows Server 2. R2, Microsoft Windows Server 2. R2, Microsoft Windows Server 2. Language. English, Arabic, Dutch, French, German, Portuguese, Spanish, Korean, Russian, Italian, Greek, Hebrew, Estonian, Cantonese, Multilingual, Hindi, Welsh, Swedish, Turkish, Mandarin, Chinese. Free download Microsoft Office Professional Plus 2010 for Windows, Microsoft Office Professional Plus 2010 was the latest version of the MS Office Suite that was. How to download and install Microsoft Office 2010 for free without product keys. Duration 717. KZ Tech Flow 316,750 views. Direct Download Links Microsoft Office 2013 Professional Plus, Visio 2013 and Project 2013 Free Trial Recently we posted about the free 60day trial version of.
Microsoft Office 2. Professional Plus 3. Windows. Operating Systems. Microsoft Windows 1. Microsoft Windows 7, Microsoft Windows 8, Microsoft Windows 8. Microsoft Windows Server 2. Microsoft Windows 1. Microsoft Windows 7 6. Microsoft Windows 8 6. Microsoft Windows 8. Microsoft Windows Server 2. R2, Microsoft Windows Server 2. R2, Microsoft Windows Server 2. Language. English, Arabic, Dutch, French, German, Portuguese, Spanish, Korean, Russian, Italian, Greek, Hebrew, Estonian, Cantonese, Multilingual, Hindi, Welsh, Swedish, Turkish, Mandarin, Chinese. Free download Microsoft Office Professional Plus 2010 for Windows, Microsoft Office Professional Plus 2010 was the latest version of the MS Office Suite that was. How to download and install Microsoft Office 2010 for free without product keys. Duration 717. KZ Tech Flow 316,750 views. Direct Download Links Microsoft Office 2013 Professional Plus, Visio 2013 and Project 2013 Free Trial Recently we posted about the free 60day trial version of.
Internet Speed Tracker Internet Explorer Toolbar by Mindspark Interactive Network. What is Internet Speed Tracker Internet Explorer ToolbarFrom the Terms of Service As part of the download process for the Toolbar, you may be given the option to reset your Internet browsers homepage to an Ask homepage product andor reset your new tab page to an Ask new tab product. If you do not wish to reset your homepage andor new tab page to the Ask homepage andor Ask new tab products, you can declineopt out of these features by checking or unchecking the appropriate boxes during the download process for the Toolbar. About from Mindspark Interactive NetworkCertain versions of the Toolbar may include features of or links to one or more of Mindsparks Fun. METAINFMANIFEST. MFdocmanual. htmindex. htm main. htm docrelnotesmissing. htm Release Notes Missing Features Release 7. 30 December 12, 2012. Incredimail is an email program that offers lots of animated characters, also called notifiers, to announce when you have mail. It also offers a wide array of other. Database of over 45K programs that can run on a Windows 1087VistaXP system at startup, including those created by viruses, worms, spyware, and trojans.  Web. Products suite of websites and applications or other Mindspark or Mindspark affiliate provided websites or products. The Fun. Web. Products applications include Webfetti, Zwinky, My. Fun. Cards, Popular Screensavers, Curs. Read more. Overview. Upon installation and setup, it defines an auto start registry entry which makes this program run on each Windows boot for all user logins. It adds a background controller service that is set to automatically run. Delaying the start of this service is possible through the service manager. The program adds a toolbar to Microsoft Internet Explorer. A scheduled task is added to Windows Task Scheduler in order to launch the program at various scheduled times the schedule varies depending on the version. The main program executable is 9t. Bar. dll. A vast majority of those who have this installed end up removing it just after a couple weeks. The software installer includes 8. MB 1. 0,6. 89,9. Possible malware installed by this program. Automatically starts with Windows. Loads into the web browser.
Web. Products suite of websites and applications or other Mindspark or Mindspark affiliate provided websites or products. The Fun. Web. Products applications include Webfetti, Zwinky, My. Fun. Cards, Popular Screensavers, Curs. Read more. Overview. Upon installation and setup, it defines an auto start registry entry which makes this program run on each Windows boot for all user logins. It adds a background controller service that is set to automatically run. Delaying the start of this service is possible through the service manager. The program adds a toolbar to Microsoft Internet Explorer. A scheduled task is added to Windows Task Scheduler in order to launch the program at various scheduled times the schedule varies depending on the version. The main program executable is 9t. Bar. dll. A vast majority of those who have this installed end up removing it just after a couple weeks. The software installer includes 8. MB 1. 0,6. 89,9. Possible malware installed by this program. Automatically starts with Windows. Loads into the web browser.  Installs a Windows Service. Many experts agree, if you dont use it you should remove it Warning, multiple anti virus scanners have detected possible malware in Internet Speed Tracker Internet Explorer Toolbar. Bar. dll3f. 75. 83. Anti Virus software. Version. Detectionavast Win. 32 Mindspark A PUPAVG2. Zango. Kingsoft Anti. Virus. 33. 10. 20. Win. 32. Troj. Undef. kcloudMc. Afee. 56. 00. 7. 25. Artemis 3. F7. 58. Mc. Afee GW Edition. Artemis 3. F7. 58. Trend. Micro House. Call. 7. 2. 1. 1TROJGEN. F4. 7V1. 20. 8VIPRE Antivirus. My. Web. Search. J v not malicious9t. Src. As. dll7. 79. Anti Virus software. Software version. Detection. Ahn. Lab V3. PUPWin. 32. My. Web. Search. Antiy AVL1. Risk. WareWeb. Toolbar not a virusWin. My. Web. SearchavastWin. 32 Mindspark A PUPAVG1. My. Web. Search. AVware. My. Web. Search. J vBaidu International. Adware. Win. 32. My. Web. Search. a. Rm. SESET NOD3. 21. 05. Win. 32Toolbar. My. Web. Search. ACFortinet Forti. Gate. 5. 1. 1. 52. RiskwareMy. Web. Search. G Data. 24. Win. 32. Adware. Mindspark. CKaspersky. 12. 0. Web. Toolbar. Win. My. Web. Search. si. Kingsoft Anti. Virus. Win. 32. Troj. My. Web. Search. si. kcloudMalwarebytes. PUP. Optional. Mind. Spark. NANO Anti. Virus. 0. 2. 8. 2. Riskware. Win. 32. Toolbar. dfqike. Qihoo 3. Win. 32Virus. Web. Toolbar. 3. 0b. Tencent. Win. 32. Trojan. Falsesign. Aisc. Trend. Micro House. Call. 9. 7. 00. 0. SuspiciousGEN. F4. V0. 81. 2VIPRE Antivirus. My. Web. Search. J v not maliciousZillya. Adware. My. Web. Search. Win. 32. 9. 02. 9tbarsvc. Anti Virus software. Software version. Detection. Agnitum Outpost. PUA. Toolbar. My. Web. Search Ahn. Lab V3. 20. 14. 1. PUPWin. 32. My. Web. Search. Antiy AVL1. Risk. WareWeb. Toolbar not a virusWin. My. Web. Searchavast Win. 32 Mindspark A PUPAVG1. My. Web. Search. AVware. My. Web. Search. J vBaidu International. Adware. Win. 32. My. Web. Search. a. IESET NOD3. Win. 32Toolbar. My. Web. Search. AEFortinet Forti. Gate. 5. 0. 9. 99. RiskwareMy. Web. Search. G Data. 24. Win. 32. Adware. Mindspark. CKaspersky. 12. 0. Web. Toolbar. Win. My. Web. Search. si. Kingsoft Anti. Virus. Win. 32. Troj. My. Web. Search. si. kcloudMalwarebytes. PUP. Optional. Mind. Spark. NANO Anti. Virus. 0. 2. 8. 6. Riskware. Win. 32. Toolbar. dfqijl. Qihoo 3. Win. 32Virus. Web. Toolbar. 3. 0b. Tencent. Win. 32. Trojan. Falsesign. Pgms. VIPRE Antivirus. My. Web. Search. J v not maliciousZillya. Adware. My. Web. Search. Win. 32. 1. 22. 89t. Srch. Mn. exe3c. Anti Virus software. Software version. Detection. Ahn. Lab V3. TrojanWin. 32. Buzus. Antiy AVL1. 0. 0. Risk. WareWeb. Toolbar not a virusWin. My. Web. Searchavast Win. 32 Mindspark A PUPAVG1. My. Web. Search. AVware. My. Web. Search. J vBaidu International. Adware. Win. 32. My. Web. Search. ab. ZESET NOD3. Win. 32Toolbar. My. Web. Search. AJFortinet Forti. Gate. 5. 0. 9. 99. RiskwareMy. Web. Search. G Data. 24. Win. 32. Adware. Mindspark. CKaspersky. 12. 0. Web. Toolbar. Win. My. Web. Search. si. Kingsoft Anti. Virus. Win. 32. Troj. My. Web. Search. si. kcloudMalwarebytes. PUP. Optional. Mind. Spark. Qihoo 3. 60. Win. 32Virus. Web. Toolbar. 3. 0b. Tencent. Win. 32. Trojan. Falsesign. Lmut. VIPRE Antivirus. My. Web. Search. J v not maliciousZillya. Adware. My. Web. Search. Win. 32. 1. 35. 1APPINTEGRATOR. EXEb. 69. 40fe. 9d. Anti Virus software. Software version. Detection. Ahn. Lab V3. My. Web. Search. J vBaidu International. Adware. Win. 32. My. Web. Search. am. ESET NOD3. Win. 32Toolbar. My. CKaspersky. 12. 0. Web. Toolbar. Win. My. Web. Search. si. Kingsoft Anti. Virus. Win. 32. Troj. My. Web. Search. si. kcloudMalwarebytes. PUP. Optional. Mind. Spark. Qihoo 3. 60. Win. 32Virus. Web. Toolbar. 3. 0b. Tencent. Win. 32. Trojan. Falsesign. Pgcq. Trend. Micro House. Call. 9. 7. 00. 0. SuspiciousGEN. F4. V0. 81. 2VIPRE Antivirus. My. Web. Search. J v not malicious9tmedint. Anti Virus software. Software version. Detection. Ahn. Lab V3. PUPWin. 32. My. Web. Searchavast 8. 0. Win. 32 Mindspark A PUPAVG1. My. Web. Search. AVware. My. Web. Search. J vBaidu International. Adware. Win. 32. My. Web. Search. b. QESET NOD3. Win. 32Toolbar. My. Web. Search. AJFortinet Forti. Gate. 5. 0. 9. 99. RiskwareMy. Web. Search. G Data. 24. Win. 32. Adware. Mindspark. CKaspersky. 12. 0. Web. Toolbar. Win. My. Web. Search. si. Kingsoft Anti. Virus. Win. 32. Troj. My. Web. Search. si. kcloudMalwarebytes. PUP. Optional. Mind. Spark. Qihoo 3. 60. Win. 32Virus. Web. Toolbar. 3. 0b. Tencent. Win. 32. Trojan. Falsesign. Pial. VIPRE Antivirus. My. Web. Search. J v not maliciousZillya. Adware. My. Web. Search. Win. 32. 1. 39. 2App. Integrator. 64. exe1. Anti Virus software. Software version. Detection. Ahn. Lab V3. PUPWin. 32. My. Web. Search. Antiy AVL1. Risk. WareWeb. Toolbar not a virusWin. My. Web. Searchavast Win. 32 Mindspark A PUPAVG1. Zango. Baidu International. Adware. Win. 32. My. Web. Search. Aki. Fortinet Forti. Gate. RiskwareMy. Web. Search. Kaspersky. Web. Toolbar. Win. My. Web. Search. si. Malwarebytes. 1. 7. PUP. Optional. Mind. Spark. Panda Antivirus. AdwareWeb. Search. Qihoo 3. 60. 1. 0. Win. 32Virus. Web. Toolbar. 3. 0b. Tencent. Win. 32. Trojan. Falsesign. Dvqb. VIPRE Antivirus. My. Web. Search. J v not maliciousNP9t. Stub. dll4. 96. 13b. Anti Virus software. Software version. Detectionavast 8. Win. 32 Mindspark A PUPAVG1. Zango. Kingsoft Anti. Virus. 20. 13. 0. Win. 32. Troj. Undef. kcloudVIPRE Antivirus.
Installs a Windows Service. Many experts agree, if you dont use it you should remove it Warning, multiple anti virus scanners have detected possible malware in Internet Speed Tracker Internet Explorer Toolbar. Bar. dll3f. 75. 83. Anti Virus software. Version. Detectionavast Win. 32 Mindspark A PUPAVG2. Zango. Kingsoft Anti. Virus. 33. 10. 20. Win. 32. Troj. Undef. kcloudMc. Afee. 56. 00. 7. 25. Artemis 3. F7. 58. Mc. Afee GW Edition. Artemis 3. F7. 58. Trend. Micro House. Call. 7. 2. 1. 1TROJGEN. F4. 7V1. 20. 8VIPRE Antivirus. My. Web. Search. J v not malicious9t. Src. As. dll7. 79. Anti Virus software. Software version. Detection. Ahn. Lab V3. PUPWin. 32. My. Web. Search. Antiy AVL1. Risk. WareWeb. Toolbar not a virusWin. My. Web. SearchavastWin. 32 Mindspark A PUPAVG1. My. Web. Search. AVware. My. Web. Search. J vBaidu International. Adware. Win. 32. My. Web. Search. a. Rm. SESET NOD3. 21. 05. Win. 32Toolbar. My. Web. Search. ACFortinet Forti. Gate. 5. 1. 1. 52. RiskwareMy. Web. Search. G Data. 24. Win. 32. Adware. Mindspark. CKaspersky. 12. 0. Web. Toolbar. Win. My. Web. Search. si. Kingsoft Anti. Virus. Win. 32. Troj. My. Web. Search. si. kcloudMalwarebytes. PUP. Optional. Mind. Spark. NANO Anti. Virus. 0. 2. 8. 2. Riskware. Win. 32. Toolbar. dfqike. Qihoo 3. Win. 32Virus. Web. Toolbar. 3. 0b. Tencent. Win. 32. Trojan. Falsesign. Aisc. Trend. Micro House. Call. 9. 7. 00. 0. SuspiciousGEN. F4. V0. 81. 2VIPRE Antivirus. My. Web. Search. J v not maliciousZillya. Adware. My. Web. Search. Win. 32. 9. 02. 9tbarsvc. Anti Virus software. Software version. Detection. Agnitum Outpost. PUA. Toolbar. My. Web. Search Ahn. Lab V3. 20. 14. 1. PUPWin. 32. My. Web. Search. Antiy AVL1. Risk. WareWeb. Toolbar not a virusWin. My. Web. Searchavast Win. 32 Mindspark A PUPAVG1. My. Web. Search. AVware. My. Web. Search. J vBaidu International. Adware. Win. 32. My. Web. Search. a. IESET NOD3. Win. 32Toolbar. My. Web. Search. AEFortinet Forti. Gate. 5. 0. 9. 99. RiskwareMy. Web. Search. G Data. 24. Win. 32. Adware. Mindspark. CKaspersky. 12. 0. Web. Toolbar. Win. My. Web. Search. si. Kingsoft Anti. Virus. Win. 32. Troj. My. Web. Search. si. kcloudMalwarebytes. PUP. Optional. Mind. Spark. NANO Anti. Virus. 0. 2. 8. 6. Riskware. Win. 32. Toolbar. dfqijl. Qihoo 3. Win. 32Virus. Web. Toolbar. 3. 0b. Tencent. Win. 32. Trojan. Falsesign. Pgms. VIPRE Antivirus. My. Web. Search. J v not maliciousZillya. Adware. My. Web. Search. Win. 32. 1. 22. 89t. Srch. Mn. exe3c. Anti Virus software. Software version. Detection. Ahn. Lab V3. TrojanWin. 32. Buzus. Antiy AVL1. 0. 0. Risk. WareWeb. Toolbar not a virusWin. My. Web. Searchavast Win. 32 Mindspark A PUPAVG1. My. Web. Search. AVware. My. Web. Search. J vBaidu International. Adware. Win. 32. My. Web. Search. ab. ZESET NOD3. Win. 32Toolbar. My. Web. Search. AJFortinet Forti. Gate. 5. 0. 9. 99. RiskwareMy. Web. Search. G Data. 24. Win. 32. Adware. Mindspark. CKaspersky. 12. 0. Web. Toolbar. Win. My. Web. Search. si. Kingsoft Anti. Virus. Win. 32. Troj. My. Web. Search. si. kcloudMalwarebytes. PUP. Optional. Mind. Spark. Qihoo 3. 60. Win. 32Virus. Web. Toolbar. 3. 0b. Tencent. Win. 32. Trojan. Falsesign. Lmut. VIPRE Antivirus. My. Web. Search. J v not maliciousZillya. Adware. My. Web. Search. Win. 32. 1. 35. 1APPINTEGRATOR. EXEb. 69. 40fe. 9d. Anti Virus software. Software version. Detection. Ahn. Lab V3. My. Web. Search. J vBaidu International. Adware. Win. 32. My. Web. Search. am. ESET NOD3. Win. 32Toolbar. My. CKaspersky. 12. 0. Web. Toolbar. Win. My. Web. Search. si. Kingsoft Anti. Virus. Win. 32. Troj. My. Web. Search. si. kcloudMalwarebytes. PUP. Optional. Mind. Spark. Qihoo 3. 60. Win. 32Virus. Web. Toolbar. 3. 0b. Tencent. Win. 32. Trojan. Falsesign. Pgcq. Trend. Micro House. Call. 9. 7. 00. 0. SuspiciousGEN. F4. V0. 81. 2VIPRE Antivirus. My. Web. Search. J v not malicious9tmedint. Anti Virus software. Software version. Detection. Ahn. Lab V3. PUPWin. 32. My. Web. Searchavast 8. 0. Win. 32 Mindspark A PUPAVG1. My. Web. Search. AVware. My. Web. Search. J vBaidu International. Adware. Win. 32. My. Web. Search. b. QESET NOD3. Win. 32Toolbar. My. Web. Search. AJFortinet Forti. Gate. 5. 0. 9. 99. RiskwareMy. Web. Search. G Data. 24. Win. 32. Adware. Mindspark. CKaspersky. 12. 0. Web. Toolbar. Win. My. Web. Search. si. Kingsoft Anti. Virus. Win. 32. Troj. My. Web. Search. si. kcloudMalwarebytes. PUP. Optional. Mind. Spark. Qihoo 3. 60. Win. 32Virus. Web. Toolbar. 3. 0b. Tencent. Win. 32. Trojan. Falsesign. Pial. VIPRE Antivirus. My. Web. Search. J v not maliciousZillya. Adware. My. Web. Search. Win. 32. 1. 39. 2App. Integrator. 64. exe1. Anti Virus software. Software version. Detection. Ahn. Lab V3. PUPWin. 32. My. Web. Search. Antiy AVL1. Risk. WareWeb. Toolbar not a virusWin. My. Web. Searchavast Win. 32 Mindspark A PUPAVG1. Zango. Baidu International. Adware. Win. 32. My. Web. Search. Aki. Fortinet Forti. Gate. RiskwareMy. Web. Search. Kaspersky. Web. Toolbar. Win. My. Web. Search. si. Malwarebytes. 1. 7. PUP. Optional. Mind. Spark. Panda Antivirus. AdwareWeb. Search. Qihoo 3. 60. 1. 0. Win. 32Virus. Web. Toolbar. 3. 0b. Tencent. Win. 32. Trojan. Falsesign. Dvqb. VIPRE Antivirus. My. Web. Search. J v not maliciousNP9t. Stub. dll4. 96. 13b. Anti Virus software. Software version. Detectionavast 8. Win. 32 Mindspark A PUPAVG1. Zango. Kingsoft Anti. Virus. 20. 13. 0. Win. 32. Troj. Undef. kcloudVIPRE Antivirus.
It is actually not possible at the moment to directly modify the quantize value of an entire sample pack. If you want to do so, first duplicate the pack and then. Top VIdeos. Warning Invalid argument supplied for foreach in srvusersserverpilotappsjujaitalypublicindex. php on line 447. I dont quite see the point when one can simply use the Reapers free ReaEQ VST that has no band limitations and is also parametric. httpwww. reaper. fm. Hot spots Hot spots Hot spots Hot spots. 1 vacheron constantin gold watch 20172018 2 chopard watch on sale 20172018. How to Set Up Digital Audio in your Home Studio Ways to get audio into your computer for your creative projects by Tweak. Safety Trustworthy. How To Install Vst To Garageband Loops Tutorial
 Savannah, GA Official Website. We would like to show you a description here but the site wont allow us. 15. 11. 17 Fritz 16. Fritz 16 byl uveden na trh pesn podle plnu 14. 11. Na testy novho motoru od Vaka Rajlicha si musme pr dn pokat, nicmn. SecurityStudy. One of the Largest, Old Established Sources, of Antique and Vintage Swords, Arms, Armour And Military Books in Europe. International Journal of Engineering Research and Applications IJERA is an open access online peer reviewed international journal that publishes research. Security Services for City Hall, Gamble Building, BMB and Mobility Parking Services Event 3327.
Savannah, GA Official Website. We would like to show you a description here but the site wont allow us. 15. 11. 17 Fritz 16. Fritz 16 byl uveden na trh pesn podle plnu 14. 11. Na testy novho motoru od Vaka Rajlicha si musme pr dn pokat, nicmn. SecurityStudy. One of the Largest, Old Established Sources, of Antique and Vintage Swords, Arms, Armour And Military Books in Europe. International Journal of Engineering Research and Applications IJERA is an open access online peer reviewed international journal that publishes research. Security Services for City Hall, Gamble Building, BMB and Mobility Parking Services Event 3327.
Sources. For most Unix systems, you must download and compile the source code. The same source code archive can also be used to build the Windows and Mac versions. ASUS Treiber Download Download Treiber for Windows XP, Vista, 7 8. Warum ist es so wichtig, Treiber aktuell zu haltenInformationWeek. com News, analysis and research for business technology professionals, plus peertopeer knowledge sharing. Engage with our community. Hier sind die direkt download Links fr Windows 7 Starter, Home Basic Premium, Professional und Ultimate mit und ohne Win7 Service PackWann auch immer ein Hersteller eine neue Hardware verffentlicht, wird er auch kompatible Treiber herausbringen, damit die Hardware ordnungsgem funktioniert. Tage und Wochen hinweg wird der Hersteller sehr wahrscheinlich aktualisierte Treiber verffentlichen, um neue und unvorhergesehene Fehler zu beheben. Alte. Treiber werden die Leistung des Computers beeintrchtigen und die Hardware wird nicht in der Lage sein, Top Leistung zu erbringen. Treiber knnen sogar zu Systemfehlern fhren.  Hardware Hersteller knnten auch Extra Features zu aktualisierten Treibern fr neue Spiele hinzufgen, um das Gameplay und die Graphiken zu verbessern. In anderen Worten, aktualisierte Treiber stellen sicher, dass Ihr Computer optimal luft. Wie oft sollte ich meine Treiber aktualisieren Hardware Hersteller bringen neue Treiber regelmig zu bestimmten Zeitpunkten heraus. Zum Beispiel verffentlichen bekanntere Unternehmen alle 2 Wochen oder jeden Monat neue Treiber, ganz besonders, wenn neue Betriebssysteme auf den Markt gebracht werden, wie zum Beispiel das neue Windows 8. Hersteller werden hufig Treiber aktualisieren, um alle mglichen Fehler zu beheben, sowie neue Features hinzuzufgen, sodass neue Systeme untersttzt werden. Wir empfehlen, einmal pro Monat nach Aktualisierungen zu scannen.
Hardware Hersteller knnten auch Extra Features zu aktualisierten Treibern fr neue Spiele hinzufgen, um das Gameplay und die Graphiken zu verbessern. In anderen Worten, aktualisierte Treiber stellen sicher, dass Ihr Computer optimal luft. Wie oft sollte ich meine Treiber aktualisieren Hardware Hersteller bringen neue Treiber regelmig zu bestimmten Zeitpunkten heraus. Zum Beispiel verffentlichen bekanntere Unternehmen alle 2 Wochen oder jeden Monat neue Treiber, ganz besonders, wenn neue Betriebssysteme auf den Markt gebracht werden, wie zum Beispiel das neue Windows 8. Hersteller werden hufig Treiber aktualisieren, um alle mglichen Fehler zu beheben, sowie neue Features hinzuzufgen, sodass neue Systeme untersttzt werden. Wir empfehlen, einmal pro Monat nach Aktualisierungen zu scannen.  Wussten Sie, dass Windows 7 mit der Zeit immer langsamer wird In 16 Schritten lernen Sie Windows 7 auf Ihrem Computer zu beschleunigen. Download Games Torrents for PC, XBOX 360, XBOX ONE, PS2, PS3, PS4, PSP, PS Vita, Linux, Macintosh, Nintendo Wii, Nintendo Wii U, Nintendo 3DS. For free UpdateStar is compatible with Windows platforms. UpdateStar has been tested to meet all of the technical requirements to be compatible with Windows 10, 8. 1, Windows 8. SubversionServer unter Windows installieren. Heute zeige ich euch, wie man einen SubversionServer unter Windows installiert, diesen automatisch mit dem System.
Wussten Sie, dass Windows 7 mit der Zeit immer langsamer wird In 16 Schritten lernen Sie Windows 7 auf Ihrem Computer zu beschleunigen. Download Games Torrents for PC, XBOX 360, XBOX ONE, PS2, PS3, PS4, PSP, PS Vita, Linux, Macintosh, Nintendo Wii, Nintendo Wii U, Nintendo 3DS. For free UpdateStar is compatible with Windows platforms. UpdateStar has been tested to meet all of the technical requirements to be compatible with Windows 10, 8. 1, Windows 8. SubversionServer unter Windows installieren. Heute zeige ich euch, wie man einen SubversionServer unter Windows installiert, diesen automatisch mit dem System. 
NORMA Oficial Mexicana NOM 0. SSA1 2. 01. 5, Buenas prcticas de fabricacin de medicamentos. MIKEL ANDONI ARRIOLA PEALOSA, Comisionado Federal para la Proteccin contra Riesgos Sanitarios y Presidente del Comit Consultivo Nacional de Normalizacin de Regulacin y Fomento Sanitario, con fundamento en los artculos 3. Ley Orgnica de la Administracin Pblica Federal 4, de la Ley Federal de Procedimiento Administrativo 3o, fracciones XXII y XXIV, 1. A, fraccin I, 1. III, 1. 94, 1. 94 Bis, 1. Bis de la Ley General de Salud 3. II, 3. 9, fraccin V, 4. I, V, XI y XII, 4. IV, de la Ley Federal sobre Metrologa y Normalizacin 9, 1.  Reglamento de Insumos para la Salud 2. Reglamento de la Ley Federal sobre Metrologa y Normalizacin, y 3, fracciones I, literal b y II y 1. IV y VIII, del Reglamento de la Comisin Federal para Proteccin contra Riesgos Sanitarios, y. CONSIDERANDOQue en cumplimiento a lo previsto en el artculo 4.
Reglamento de Insumos para la Salud 2. Reglamento de la Ley Federal sobre Metrologa y Normalizacin, y 3, fracciones I, literal b y II y 1. IV y VIII, del Reglamento de la Comisin Federal para Proteccin contra Riesgos Sanitarios, y. CONSIDERANDOQue en cumplimiento a lo previsto en el artculo 4.  Estoy haciendo mi tesis de grado en visual fox pro, ya casi la termino, necesito saber como pasar datos almacenados en variables publicas a un grid, y tambien datos. I, de la Ley Federal sobre Metrologa y Normalizacin, el 3. Comit Consultivo Nacional de Normalizacin de Regulacin y Fomento Sanitario, el anteproyecto de la presente Norma Que con fecha 9 de septiembre de 2. Comit Consultivo Nacional de Normalizacin de Regulacin y Fomento Sanitario y de lo previsto en el artculo 4. I de la Ley Federal sobre Metrologa y Normalizacin, se public en el Diario Oficial de la Federacin, el Proyecto de la presente Norma, a efecto de que dentro de los siguientes sesenta das naturales posteriores a dicha publicacin, los interesados presentaran sus comentarios al Comit antes sealado Que con fecha previa, fue publicada en el Diario Oficial de la Federacin, la respuesta a los comentarios recibidos por el mencionado Comit, en los trminos del artculo 4. III de la Ley Federal sobre Metrologa y Normalizacin, y. Que en atencin a las anteriores consideraciones, contando con la aprobacin del Comit Consultivo Nacional de Normalizacin de Regulacin y Fomento Sanitario, he tenido a bien expedir y ordenar la publicacin en el Diario Oficial de la Federacin de la NORMA OFICIAL MEXICANA NOM 0. SSA1 2. 01. 5, BUENAS PRCTICAS DE FABRICACIN DE MEDICAMENTOSPREFACIOEn la elaboracin de esta Norma participaron las siguientes instituciones y organismos SECRETARA DE SALUD. Comisin Federal para la Proteccin contra Riesgos Sanitarios. Comisin Permanente de la Farmacopea de los Estados Unidos Mexicanos. CONSEJO DE SALUBRIDAD GENERAL. Comisin Interinstitucional del Cuadro Bsico de Insumos del Sector Salud. Captulo 0. Introduccin. La Diabetes Mellitus es una enfermedad crnica que afecta a un nmero muy importante de personas se prev que en el ao 2010 haya. INSTITUTO MEXICANO DEL SEGURO SOCIAL. Divisin Institucional de Cuadros Bsicos de Insumos para la Salud. INSTITUTO DE SEGURIDAD Y SERVICIOS SOCIALES DE LOS TRABAJADORES DEL ESTADO. UNIVERSIDAD NACIONAL AUTNOMA DE MXICO. Facultad de Qumica. INSTITUTO POLITCNICO NACIONAL. Escuela Nacional de Ciencias Biolgicas. CMARA NACIONAL DE LA INDUSTRIA FARMACUTICA.
Estoy haciendo mi tesis de grado en visual fox pro, ya casi la termino, necesito saber como pasar datos almacenados en variables publicas a un grid, y tambien datos. I, de la Ley Federal sobre Metrologa y Normalizacin, el 3. Comit Consultivo Nacional de Normalizacin de Regulacin y Fomento Sanitario, el anteproyecto de la presente Norma Que con fecha 9 de septiembre de 2. Comit Consultivo Nacional de Normalizacin de Regulacin y Fomento Sanitario y de lo previsto en el artculo 4. I de la Ley Federal sobre Metrologa y Normalizacin, se public en el Diario Oficial de la Federacin, el Proyecto de la presente Norma, a efecto de que dentro de los siguientes sesenta das naturales posteriores a dicha publicacin, los interesados presentaran sus comentarios al Comit antes sealado Que con fecha previa, fue publicada en el Diario Oficial de la Federacin, la respuesta a los comentarios recibidos por el mencionado Comit, en los trminos del artculo 4. III de la Ley Federal sobre Metrologa y Normalizacin, y. Que en atencin a las anteriores consideraciones, contando con la aprobacin del Comit Consultivo Nacional de Normalizacin de Regulacin y Fomento Sanitario, he tenido a bien expedir y ordenar la publicacin en el Diario Oficial de la Federacin de la NORMA OFICIAL MEXICANA NOM 0. SSA1 2. 01. 5, BUENAS PRCTICAS DE FABRICACIN DE MEDICAMENTOSPREFACIOEn la elaboracin de esta Norma participaron las siguientes instituciones y organismos SECRETARA DE SALUD. Comisin Federal para la Proteccin contra Riesgos Sanitarios. Comisin Permanente de la Farmacopea de los Estados Unidos Mexicanos. CONSEJO DE SALUBRIDAD GENERAL. Comisin Interinstitucional del Cuadro Bsico de Insumos del Sector Salud. Captulo 0. Introduccin. La Diabetes Mellitus es una enfermedad crnica que afecta a un nmero muy importante de personas se prev que en el ao 2010 haya. INSTITUTO MEXICANO DEL SEGURO SOCIAL. Divisin Institucional de Cuadros Bsicos de Insumos para la Salud. INSTITUTO DE SEGURIDAD Y SERVICIOS SOCIALES DE LOS TRABAJADORES DEL ESTADO. UNIVERSIDAD NACIONAL AUTNOMA DE MXICO. Facultad de Qumica. INSTITUTO POLITCNICO NACIONAL. Escuela Nacional de Ciencias Biolgicas. CMARA NACIONAL DE LA INDUSTRIA FARMACUTICA.  CMARA NACIONAL DE LA INDUSTRIA DE LA TRANSFORMACIN. Sector mdico. ACADEMIA NACIONAL DE CIENCIAS FARMACUTICAS. A. C. ASOCIACIN FARMACUTICA MEXICANA. A. C. COLEGIO NACIONAL DE QUMICOS FARMACUTICOS BILOGOS MXICO. A. C. PRODUCCIN QUMICO FARMACUTICA. NORMA Oficial Mexicana NOM059SSA12015, Buenas prcticas de fabricacin de medicamentos. Al margen un sello con el Escudo Nacional, que dice Estados Unidos. Algunas solicitudes de colegas relacionadas al costo reglas y cdigos en NAFA ASSOCIATION para hacer una revalida a la practica de la abogaca requieren la. Luego de obtener una billetera o cartera Bitcoin, hay varias maneras de obtener Bitcoins. Busque vacantes. Palabra clave Discapacidad. A program of study that involves a multiyear sequence of courses that integrates core academic knowledge with technical and occupational knowledge to provide students. UNIVERSIDAD COMPLUTENSE DE MADRID. FACULTAD DE CIENCIAS QUMICAS Departamento de Ingeniera Qumica TESIS DOCTORAL Estudio de la influencia de las materias primas. Top VIdeos. Warning Invalid argument supplied for foreach in srvusersserverpilotappsjujaitalypublicindex. php on line 447. A. C. ASOCIACIN MEXICANA DE LABORATORIOS FARMACUTICOS. A. C. ASOCIACIN MEXICANA DE INDUSTRIAS DE INVESTIGACIN FARMACUTICA. A. C. ASOCIACIN NACIONAL DE FABRICANTES DE MEDICAMENTOS. A. C. ASOCIACIN NACIONAL DE LA INDUSTRIA FARMACUTICA HOMEOPTICA. A. C. NDICE1. Objetivo y campo de aplicacin. Referencias. 3. Definiciones. Smbolos y abreviaturas. Sistema de Gestin de Calidad. Gestin de Riesgos de Calidad. Personal. 8. Instalaciones y equipo. Calificacin y validacin. Sistemas de fabricacin. Laboratorio de Control de Calidad. Liberacin de producto terminado. Retiro de Producto del Mercado. Actividades subcontratadas. Destino Final de residuos. Buenas Prcticas de Almacenamiento y Distribucin. Concordancia con normas internacionales y mexicanas. Bibliografa. 1. 9. Observancia. 2. 0. Vigencia. 2. 1. Apndices. Apndice A Normativo. Clasificacin de reas de fabricacin. Apndice B Normativo. Revisin Anual del Producto. Objetivo y campo de aplicacin. Objetivo. Esta Norma establece los requisitos mnimos necesarios para el proceso de fabricacin de los medicamentos para uso humano comercializados en el pas yo con fines de investigacin. Campo de aplicacin. Esta Norma es de observancia obligatoria para todos los establecimientos dedicados a la fabricacin yo importacin de medicamentos para uso humano comercializados en el pas yo con fines de investigacin, as como los laboratorios de control de calidad, almacenes de acondicionamiento, depsito y distribucin de medicamentos y materias primas para su elaboracin. Referencias. Para la correcta aplicacin de esta Norma, es necesario consultar las siguientes normas oficiales mexicanas o las que las sustituyan 2. Norma Oficial Mexicana NOM 0. SCT2. 00. 9, Listado de las substancias y materiales peligrosos ms usualmente transportados, instrucciones y uso de envases y embalajes, recipientes intermedios para graneles RIG S, grandes envases y embalajes, cisternas porttiles, contenedores de gas de elementos mltiples y contenedores para graneles para el transporte de materiales y residuos peligrosos. Norma Oficial Mexicana NOM 0. SEMARNAT 1. 99. 6, Que establece los lmites mximos permisibles de contaminantes en las descargas de aguas residuales a los sistemas de alcantarillado urbano o municipal. Norma Oficial Mexicana NOM 0. STPS 1. 99. 8, Relativa a las condiciones de seguridad e higiene en los centros de trabajo para el manejo, transporte y almacenamiento de sustancias qumicas peligrosas. Norma Oficial Mexicana NOM 0. STPS 2. 01. 1, Recipientes sujetos a presin, recipientes criognicos y generadores de vapor o calderas Funcionamiento Condiciones de Seguridad. Norma Oficial Mexicana NOM 0. STPS 2. 00. 8, Colores y seales de seguridad e higiene, e identificacin de riesgos por fluidos conducidos en tuberas. Norma Oficial Mexicana NOM 0. SEMARNAT 2. 00. 5, Que establece las caractersticas, el procedimiento de identificacin, clasificacin y los listados de los residuos peligrosos. Norma Oficial Mexicana NOM 0. ZOO 1. 99. 9, Especificaciones tcnicas para la produccin, cuidado y uso de los animales de laboratorio. Norma Oficial Mexicana NOM 0. SSA1 2. 01. 2, Etiquetado de medicamentos y de remedios herbolarios. Norma Oficial Mexicana NOM 0. SSA1 2. 00. 5, Estabilidad de frmacos y medicamentos. Norma Oficial Mexicana NOM 0. SEMARNAT SSA1 2. Proteccin ambiental Salud ambiental Residuos peligrosos biolgico infecciosos Clasificacin y especificaciones de manejo. Norma Oficial Mexicana NOM 1. SSA1 2. 01. 3, Buenas prcticas de fabricacin para frmacos. Norma Oficial Mexicana NOM 2. SSA1 2. 01. 2, Instalacin y operacin de la farmacovigilancia. Norma Oficial Mexicana NOM 2. SSA1 2. 01. 2, Buenas prcticas de fabricacin para establecimientos dedicados a la fabricacin de dispositivos mdicos. Norma Oficial Mexicana NOM 2. SSA1 2. 01. 2, Para la disposicin de sangre humana y sus componentes con fines teraputicos. Norma Oficial Mexicana NOM 2. SSA1 2. 01. 4, En materia de medicamentos biotecnolgicos. Norma Oficial Mexicana NOM 0. STPS 2. 01. 1. Recipientes sujetos a presin, recipientes criognicos y generadores de vapor o calderas Funcionamiento Condiciones de seguridad. Definiciones. Para efectos de esta Norma, se entiende por 3.
CMARA NACIONAL DE LA INDUSTRIA DE LA TRANSFORMACIN. Sector mdico. ACADEMIA NACIONAL DE CIENCIAS FARMACUTICAS. A. C. ASOCIACIN FARMACUTICA MEXICANA. A. C. COLEGIO NACIONAL DE QUMICOS FARMACUTICOS BILOGOS MXICO. A. C. PRODUCCIN QUMICO FARMACUTICA. NORMA Oficial Mexicana NOM059SSA12015, Buenas prcticas de fabricacin de medicamentos. Al margen un sello con el Escudo Nacional, que dice Estados Unidos. Algunas solicitudes de colegas relacionadas al costo reglas y cdigos en NAFA ASSOCIATION para hacer una revalida a la practica de la abogaca requieren la. Luego de obtener una billetera o cartera Bitcoin, hay varias maneras de obtener Bitcoins. Busque vacantes. Palabra clave Discapacidad. A program of study that involves a multiyear sequence of courses that integrates core academic knowledge with technical and occupational knowledge to provide students. UNIVERSIDAD COMPLUTENSE DE MADRID. FACULTAD DE CIENCIAS QUMICAS Departamento de Ingeniera Qumica TESIS DOCTORAL Estudio de la influencia de las materias primas. Top VIdeos. Warning Invalid argument supplied for foreach in srvusersserverpilotappsjujaitalypublicindex. php on line 447. A. C. ASOCIACIN MEXICANA DE LABORATORIOS FARMACUTICOS. A. C. ASOCIACIN MEXICANA DE INDUSTRIAS DE INVESTIGACIN FARMACUTICA. A. C. ASOCIACIN NACIONAL DE FABRICANTES DE MEDICAMENTOS. A. C. ASOCIACIN NACIONAL DE LA INDUSTRIA FARMACUTICA HOMEOPTICA. A. C. NDICE1. Objetivo y campo de aplicacin. Referencias. 3. Definiciones. Smbolos y abreviaturas. Sistema de Gestin de Calidad. Gestin de Riesgos de Calidad. Personal. 8. Instalaciones y equipo. Calificacin y validacin. Sistemas de fabricacin. Laboratorio de Control de Calidad. Liberacin de producto terminado. Retiro de Producto del Mercado. Actividades subcontratadas. Destino Final de residuos. Buenas Prcticas de Almacenamiento y Distribucin. Concordancia con normas internacionales y mexicanas. Bibliografa. 1. 9. Observancia. 2. 0. Vigencia. 2. 1. Apndices. Apndice A Normativo. Clasificacin de reas de fabricacin. Apndice B Normativo. Revisin Anual del Producto. Objetivo y campo de aplicacin. Objetivo. Esta Norma establece los requisitos mnimos necesarios para el proceso de fabricacin de los medicamentos para uso humano comercializados en el pas yo con fines de investigacin. Campo de aplicacin. Esta Norma es de observancia obligatoria para todos los establecimientos dedicados a la fabricacin yo importacin de medicamentos para uso humano comercializados en el pas yo con fines de investigacin, as como los laboratorios de control de calidad, almacenes de acondicionamiento, depsito y distribucin de medicamentos y materias primas para su elaboracin. Referencias. Para la correcta aplicacin de esta Norma, es necesario consultar las siguientes normas oficiales mexicanas o las que las sustituyan 2. Norma Oficial Mexicana NOM 0. SCT2. 00. 9, Listado de las substancias y materiales peligrosos ms usualmente transportados, instrucciones y uso de envases y embalajes, recipientes intermedios para graneles RIG S, grandes envases y embalajes, cisternas porttiles, contenedores de gas de elementos mltiples y contenedores para graneles para el transporte de materiales y residuos peligrosos. Norma Oficial Mexicana NOM 0. SEMARNAT 1. 99. 6, Que establece los lmites mximos permisibles de contaminantes en las descargas de aguas residuales a los sistemas de alcantarillado urbano o municipal. Norma Oficial Mexicana NOM 0. STPS 1. 99. 8, Relativa a las condiciones de seguridad e higiene en los centros de trabajo para el manejo, transporte y almacenamiento de sustancias qumicas peligrosas. Norma Oficial Mexicana NOM 0. STPS 2. 01. 1, Recipientes sujetos a presin, recipientes criognicos y generadores de vapor o calderas Funcionamiento Condiciones de Seguridad. Norma Oficial Mexicana NOM 0. STPS 2. 00. 8, Colores y seales de seguridad e higiene, e identificacin de riesgos por fluidos conducidos en tuberas. Norma Oficial Mexicana NOM 0. SEMARNAT 2. 00. 5, Que establece las caractersticas, el procedimiento de identificacin, clasificacin y los listados de los residuos peligrosos. Norma Oficial Mexicana NOM 0. ZOO 1. 99. 9, Especificaciones tcnicas para la produccin, cuidado y uso de los animales de laboratorio. Norma Oficial Mexicana NOM 0. SSA1 2. 01. 2, Etiquetado de medicamentos y de remedios herbolarios. Norma Oficial Mexicana NOM 0. SSA1 2. 00. 5, Estabilidad de frmacos y medicamentos. Norma Oficial Mexicana NOM 0. SEMARNAT SSA1 2. Proteccin ambiental Salud ambiental Residuos peligrosos biolgico infecciosos Clasificacin y especificaciones de manejo. Norma Oficial Mexicana NOM 1. SSA1 2. 01. 3, Buenas prcticas de fabricacin para frmacos. Norma Oficial Mexicana NOM 2. SSA1 2. 01. 2, Instalacin y operacin de la farmacovigilancia. Norma Oficial Mexicana NOM 2. SSA1 2. 01. 2, Buenas prcticas de fabricacin para establecimientos dedicados a la fabricacin de dispositivos mdicos. Norma Oficial Mexicana NOM 2. SSA1 2. 01. 2, Para la disposicin de sangre humana y sus componentes con fines teraputicos. Norma Oficial Mexicana NOM 2. SSA1 2. 01. 4, En materia de medicamentos biotecnolgicos. Norma Oficial Mexicana NOM 0. STPS 2. 01. 1. Recipientes sujetos a presin, recipientes criognicos y generadores de vapor o calderas Funcionamiento Condiciones de seguridad. Definiciones. Para efectos de esta Norma, se entiende por 3.
A Solution for Mac. Book Pro Booting to a Black Screen. Rarely, a Mac may encounter some peculiar issue during system boot that can cause quite a bit of panic, like booting to a completely black screen. It would be easy to interpret that as a potential hardware problem, and in some particularly rare situations that may be the case, but its more often a software issue that can be resolved with some simple troubleshooting steps. Case in point one of our readers experience with his Mac. Book Pro, which out of the blue rebooted to a completely dark screen. Though its rare, we figured this would be a good opportunity to share three potential solutions to this problem, and similar issues, should you encounter a dark screen on system start.  First, Reset the System Management Controller to Fix the Black Display on Boot. The first thing youll want to do resolve nearly every power related issue on a Mac is to reset the SMC, or System Management Controller. This will dump and reset settings for anything power management related, and is long known to resolve problems with things like fans, heat, sleeping problems, and of course, display issues. 4. 994. 99AU7. 99 ProCam 5 is an iPhone camera app with a lot of options. Not one for minimalists, then, but the apps design is such that while it could have. Description The product is a digital alcohol tester designed for iPhone, iPad and iPod. It is equipped with a unique detector to effectively identify cigarettes, coke. We take a look at the problems and issues with the Galaxy S6 and Galaxy S6 Edge, and how you can fix them.
First, Reset the System Management Controller to Fix the Black Display on Boot. The first thing youll want to do resolve nearly every power related issue on a Mac is to reset the SMC, or System Management Controller. This will dump and reset settings for anything power management related, and is long known to resolve problems with things like fans, heat, sleeping problems, and of course, display issues. 4. 994. 99AU7. 99 ProCam 5 is an iPhone camera app with a lot of options. Not one for minimalists, then, but the apps design is such that while it could have. Description The product is a digital alcohol tester designed for iPhone, iPad and iPod. It is equipped with a unique detector to effectively identify cigarettes, coke. We take a look at the problems and issues with the Galaxy S6 and Galaxy S6 Edge, and how you can fix them. 
 On any modern Mac. Book Pro or Mac. Book Air with a built in battery, which is just a bout all of them nowadays, this is how you do that Shut down the Mac and connect it to your Mag. Safe adapter and a wall outlet as usual. Hold down the ShiftControlOptionPower button at the same time for a few seconds. Release all keys at the same time, then boot the Mac as usual. Older Macs can find directions here for the same process on their machines, its slightly different if you can take out the battery. When the Mac boots, hopefully the black screen has gone away and youre back to normal, but if it doesnt reader Nathan D. Second, Try a Keypress Sequence to Ditch the Black Screen. Regular readers may recall that we covered some OS X keyboard shortcuts for the Shutdown, Sleep, and Restart controls of just about every Mac, and this little key press sequence takes advantage of those. Oddly enough, it seems to work to resolve some of the mystery Mac booting into black screen issues. Heres the precise sequence to follow Press the Power OFF button once this will bring up the dialog box which you cant see. Press the S button this is the shortcut to sleep the Mac. Hold down the Power button until a hard shut down is forced. Wait about 1. 5 seconds, then hit the Power button again to turn it back on. This key press solution was discovered by reader Nathan D., who found it tucked away on Mac. Rumors Forums, and it has worked for several other commenters there as well. Some other users on the MR forums suggest that resetting PRAM helped them too, but most power issues are resolved by the SMC reset. Try a PRAM Reset to Resolve the Black Boot Display. If the above two tricks failed, a PRAM reset can often do the trick, as many of the commenters on this article can attest to. As a potential solution to the black screen on boot, this is done upon restarting the Mac similar to an SMC reset Reboot the Mac and as soon as you hear the boot chime, hold down the CommandOptionPR keys together. When you hear the boot sound again, the PRAM has been reset so let the Mac boot again as usual. At this point your Mac should boot again as usual and no longer have the black display, loading Mac OS or Mac OS X as usual. To stop these kinds of attacks, Google is adding a screen to the permissions process that will warn users if the app is new or unverifiedsigns that it might be. How to replace your iPhone 5 battery Remove the battery from your iPhone 5. The most frustrating thing about a phone addiction is that unlike actual substance abuse, the solution is not to stop using it completely. Instead, we have to find. Housing in the Santa Clara region of California is insanely expensive. Tech companies have taken to building modern day versions of mill towns just so their employees. A Solution for MacBook Pro Booting to a Black Screen. HOW TO Transfer Contacts From Nokia Phone To Apple iPhone Without Using Computer. by Abhishek Bhatnagar on August 26, 2009. Finally Enter Password, Hit Return. Some users in our comments report an interesting alternative finding if they hit the black screen on boot if they enter their regular login password and hit the EnterReturn key, the Mac boots up as usual and theyre good to go. Try this out, it might work for you When the Mac boots into the black screen, enter the password youd use to login to the Mac as usual. Hit the Return key. If this works, youll know rather quickly because the black screen will give way to the regular Mac OS desktop. Did one of these solutions work to get past the black screen on Mac boot for you If you happen to run into this unusual issue with your Mac, let us know how you resolved it, and if the above tips worked for your Mac. Book, Mac. Book Pro, Mac. Book Air, and whichever Pro or Air model it may be. How Google Is Stopping Phishing Attacks from Unverified Apps. Google is stepping up its effort to block phishing attempts that use app permissions to gain access to users Gmail accounts. These phishing attacks invite users to grant an app permission to manage their Google accountwhich lots of safe apps do, tooand then exploit those permissions to take over an account or send spam. To stop these kinds of attacks, Google is adding a screen to the permissions process that will warn users if the app is new or unverifiedsigns that it might be linked to a phishing attempt. The unverified app screen precedes the permissions consent screen for the app and lets potential users know that the app has yet to be verified. This will help reduce the risk of user data being phished by bad actors, Googles Naveen Agarwal and Wesley Chun wrote in a blog post announcing the change. The warning looks a little bit like Chromes warning when a sites HTTPS encryption isnt trusted. It requires users to click into advanced settings before they can commit to granting permissions to the app. Heres what the warning will look like Google recently started requiring new apps to go through a verification process to assess possible risks before being approved. In addition to the new warning system, Google will require some existing apps to undergo the verification process. The warnings and reviews are intended to shore up an area of vulnerability for Gmail users, who may not be aware of the security risks that come with granting permissions to untrusted apps. These kinds of OAuth exploits are on the rise, so its good to see Google working to prevent them.
On any modern Mac. Book Pro or Mac. Book Air with a built in battery, which is just a bout all of them nowadays, this is how you do that Shut down the Mac and connect it to your Mag. Safe adapter and a wall outlet as usual. Hold down the ShiftControlOptionPower button at the same time for a few seconds. Release all keys at the same time, then boot the Mac as usual. Older Macs can find directions here for the same process on their machines, its slightly different if you can take out the battery. When the Mac boots, hopefully the black screen has gone away and youre back to normal, but if it doesnt reader Nathan D. Second, Try a Keypress Sequence to Ditch the Black Screen. Regular readers may recall that we covered some OS X keyboard shortcuts for the Shutdown, Sleep, and Restart controls of just about every Mac, and this little key press sequence takes advantage of those. Oddly enough, it seems to work to resolve some of the mystery Mac booting into black screen issues. Heres the precise sequence to follow Press the Power OFF button once this will bring up the dialog box which you cant see. Press the S button this is the shortcut to sleep the Mac. Hold down the Power button until a hard shut down is forced. Wait about 1. 5 seconds, then hit the Power button again to turn it back on. This key press solution was discovered by reader Nathan D., who found it tucked away on Mac. Rumors Forums, and it has worked for several other commenters there as well. Some other users on the MR forums suggest that resetting PRAM helped them too, but most power issues are resolved by the SMC reset. Try a PRAM Reset to Resolve the Black Boot Display. If the above two tricks failed, a PRAM reset can often do the trick, as many of the commenters on this article can attest to. As a potential solution to the black screen on boot, this is done upon restarting the Mac similar to an SMC reset Reboot the Mac and as soon as you hear the boot chime, hold down the CommandOptionPR keys together. When you hear the boot sound again, the PRAM has been reset so let the Mac boot again as usual. At this point your Mac should boot again as usual and no longer have the black display, loading Mac OS or Mac OS X as usual. To stop these kinds of attacks, Google is adding a screen to the permissions process that will warn users if the app is new or unverifiedsigns that it might be. How to replace your iPhone 5 battery Remove the battery from your iPhone 5. The most frustrating thing about a phone addiction is that unlike actual substance abuse, the solution is not to stop using it completely. Instead, we have to find. Housing in the Santa Clara region of California is insanely expensive. Tech companies have taken to building modern day versions of mill towns just so their employees. A Solution for MacBook Pro Booting to a Black Screen. HOW TO Transfer Contacts From Nokia Phone To Apple iPhone Without Using Computer. by Abhishek Bhatnagar on August 26, 2009. Finally Enter Password, Hit Return. Some users in our comments report an interesting alternative finding if they hit the black screen on boot if they enter their regular login password and hit the EnterReturn key, the Mac boots up as usual and theyre good to go. Try this out, it might work for you When the Mac boots into the black screen, enter the password youd use to login to the Mac as usual. Hit the Return key. If this works, youll know rather quickly because the black screen will give way to the regular Mac OS desktop. Did one of these solutions work to get past the black screen on Mac boot for you If you happen to run into this unusual issue with your Mac, let us know how you resolved it, and if the above tips worked for your Mac. Book, Mac. Book Pro, Mac. Book Air, and whichever Pro or Air model it may be. How Google Is Stopping Phishing Attacks from Unverified Apps. Google is stepping up its effort to block phishing attempts that use app permissions to gain access to users Gmail accounts. These phishing attacks invite users to grant an app permission to manage their Google accountwhich lots of safe apps do, tooand then exploit those permissions to take over an account or send spam. To stop these kinds of attacks, Google is adding a screen to the permissions process that will warn users if the app is new or unverifiedsigns that it might be linked to a phishing attempt. The unverified app screen precedes the permissions consent screen for the app and lets potential users know that the app has yet to be verified. This will help reduce the risk of user data being phished by bad actors, Googles Naveen Agarwal and Wesley Chun wrote in a blog post announcing the change. The warning looks a little bit like Chromes warning when a sites HTTPS encryption isnt trusted. It requires users to click into advanced settings before they can commit to granting permissions to the app. Heres what the warning will look like Google recently started requiring new apps to go through a verification process to assess possible risks before being approved. In addition to the new warning system, Google will require some existing apps to undergo the verification process. The warnings and reviews are intended to shore up an area of vulnerability for Gmail users, who may not be aware of the security risks that come with granting permissions to untrusted apps. These kinds of OAuth exploits are on the rise, so its good to see Google working to prevent them.
Rise of the 4th Reich. Following the armistice of 1. World War I, German soldiers returned home, to a country economically devastated by the war. The Bavarian city of Munich was hit particularly hard, with jobless ex soldiers wandering the streets and a number of splinter political parties vying for membership. Hitler, unable to make a living as an artist, turned to earning extra money by serving as an army intelligence agent reporting to a Captain Karl Mayr. One day I received orders from my headquarters to find out what was behind an apparently political society which, under the name of German Workers Party, intended to hold a meeting. I was to go there and look at the society and to report upon it, Hitler recalled in Mein Kampf. Arriving at the Sterneckerbru beer hall, he was not overly impressed. I met there about 2. Hitler. However, the young military agent stood and astonished the small gathering by arguing against a proposal that Bavaria break ties with Prussia. Impressed with the nationalistic and anti Semitic views of the fledgling party, military authorities allowed Hitler to join and began funding the partys work. He became the partys seventh registered member. Critical News Headlines. 1. Irans President announced the End of the Islamic. Get the latest news and analysis in the stock market today, including national and world stock market news, business news, financial news and more. Rise of Nations also known as RON is a realtime strategy game published by Microsoft on May 20, 2003. It was developed by Big Huge Games and the develop. Following the armistice of 1918, which ended World War I, German soldiers returned home, to a country economically devastated by the war. The Bavarian city of Munich. Try out the new and improved Bubble Chart at gapminder. orgtools. Hitlers work in the party was initially supported both by funds from Captain Mayrs army intelligence unit and the dedicated anticommunists and occultists of the Thule Society. Although relegated to a minor footnote in history, the strange case of Nazi Deputy Fhrer Rudolf Hess in 1. World War II. The bushy eyebrowed Hess flew alone to England in May 1. The conventional view of the Hess flight is that of an increasingly marginalized member of Hitlers inner circle who sought to regain favor with his Fhrer by making an unauthorized visit to Britain in the hope of personally negotiating an end to the war and even enlisting En glands aid in the fight against Soviet expansionism. Hitler disavowed Hess as insane, while British prime minister Winston Churchill more kindly described Hesss attempt at negotiation as a frantic deed of lunatic benevolence. At the Nuremberg trials, Hess was found guilty of crimes against peace and spent the rest of his life a prisoner in Berlins Spandau Prison. In August 1. 98. 7, British military authorities announced that Hess had committed suicide, a judgment that continues to be disputed. Several recent studies of the Hess incident show there was much deeper meaning to this intriguing story, which was only magnified by his sudden and mysterious death just as his release from captivity seemed imminent. Rudolf Hess was born in Egypt in 1. German importer. He was well schooled and well traveled by the time he joined the German Army during World War I, serving in the same regiment as Corporal Adolf Hitler. He was wounded twice and later became a fighter pilot, but the war ended before he could experience much combat. Returning to Munich after the war, Hess helped other ex servicemen in the paramilitary Freikorps to oust a short lived Communist local government. After helping to break the Communist coup, Hess joined the Thule Society and enrolled as a student at the University of Munich, where he met his future wife and the man who was to prove a major influence on both Hitler and himself Professor General Karl Haushofer. According to author William Bramley, Professor Haushofer was a member of the Vril, another secret society based on a book by British Rosicrucian Lord Bulward Litton, about the visit of an Aryan super race to earth in the distant past. A mentor to both Hess and Hitler, Haushofer had traveled extensively in the Far East before becoming a general in the Kaisers army of World War I. His early associations with influential Japanese businessmen and statesmen were crucial in forming the German Japanese alliance of World War II, wrote author Peter Levenda. Haushofer became the first ranking Nazi to form relationships with South American governments in anticipation of a war with America. These relationships would prove instrumental in the later escape of war criminals from Europe. Haushofer, as a professor at the University of Munich, worked out Hitlers policy of Lebensraum, living space for a hemmed in Germany. Although he gained a reputation as the man behind Hitler, Haushofers views on geopolitics were largely accepted by Hitler, but only after they came from the mouth of Hess. I was only able to influence Hitler through Hess, he told his American captors in 1. Both Hess and Haushofer first met Hitler at one of the beer hall meetings of the German Workers Party. During the abortive Beer hall Putsch of 1. Nazi Party tried to seize power in Bavaria, Hess was at Hitlers side. When the coup failed, Hess drove off to Austria, where he was sheltered by members of a paramilitary wing of the Thule Society. Voluntarily returning to Germany, Hess joined Hitler in Landsberg Prison after being convicted of conspiracy to commit treason. Due to the political climate at the time, both men were released within a year. During their months of imprisonment, Hess became a close confidant to Hitler and helped produce Hitlers book, Mein Kampf. Hess edited, rewrote, and organized the book so extensively that some researchers believe he should have been credited as coauthor. As far as I know, Hess actually dictated many chapters of that book, Haushofer told interrogators in 1. Following the reorganization of the Nazi Party in 1. Hess became Hitlers private secretary. He moved upward through other major party positions until 1. Hitler became chancellor of Germany, when he was appointed Deputy Fhrer. It was Hess who initiated the Heil Hitler salute and was the first to call Hitler Mein Fhrer. Furthermore, as a member of the Geheimer Kabinettsratthe Nazi Secret Cabinet Counciland the Ministerial Council for the defense of the Reich, Hess was well aware of the secret work to develop a German atomic bomb. Proof of this knowledge came during an interview with Britains home secretary Sir John Simon, following his flight to England.
 One day sooner or later this weapon will be in our hand and. I can only say that it will be more terrible than anything that has gone before, Hess revealed. It is clear that Hess was much more powerful and well connected than is generally reported. He was the person closest to Hitler, one who shared his aspirations and beliefs. On the eve of war in 1. Hess was even named the successor to Hitler after Reichsmarschall Hermann Gring. The exceptional power and position of Rudolf Hess demands close scrutiny of his ill fated flight to En gland and its consequences. Just such a study was undertaken in 2. British authorsLynn Picknett, Clive Prince, and Stephen Prior. It soon becomes apparent that the whole Hess affair, from 1. British authorities were desperate to conceal something, they concluded. Judging by the fact that they are still desperate to conceal it, common sense dictates that they deem this secret to be unsuitable for public consumption, even after sixty years. A detailed study of Hesss flight clearly indicates that it was not just a sudden whim of an unstable individual. Explore the legacy and history of the legend. A detailed biography, interactive timeline, map, awards and honors, the Bob Marley lifestyle and more Daily paper. Local, state, and wire news and commentary. Photo galleries, business and obituaries. There is evidence of foreknowledge in Germany. Hess prepared for the flight meticulously over a period of months, even having famed aircraft designer Willy Messerschmitt modify a twin engine Messerschmitt 1. Hess also received special flight training from Messerschmitts chief test pilot, as well as Hitlers personal pilot, Hans Baur evidence that Hitler had knowledge of Hesss plans.
One day sooner or later this weapon will be in our hand and. I can only say that it will be more terrible than anything that has gone before, Hess revealed. It is clear that Hess was much more powerful and well connected than is generally reported. He was the person closest to Hitler, one who shared his aspirations and beliefs. On the eve of war in 1. Hess was even named the successor to Hitler after Reichsmarschall Hermann Gring. The exceptional power and position of Rudolf Hess demands close scrutiny of his ill fated flight to En gland and its consequences. Just such a study was undertaken in 2. British authorsLynn Picknett, Clive Prince, and Stephen Prior. It soon becomes apparent that the whole Hess affair, from 1. British authorities were desperate to conceal something, they concluded. Judging by the fact that they are still desperate to conceal it, common sense dictates that they deem this secret to be unsuitable for public consumption, even after sixty years. A detailed study of Hesss flight clearly indicates that it was not just a sudden whim of an unstable individual. Explore the legacy and history of the legend. A detailed biography, interactive timeline, map, awards and honors, the Bob Marley lifestyle and more Daily paper. Local, state, and wire news and commentary. Photo galleries, business and obituaries. There is evidence of foreknowledge in Germany. Hess prepared for the flight meticulously over a period of months, even having famed aircraft designer Willy Messerschmitt modify a twin engine Messerschmitt 1. Hess also received special flight training from Messerschmitts chief test pilot, as well as Hitlers personal pilot, Hans Baur evidence that Hitler had knowledge of Hesss plans. 
Sanitization classified information Wikipedia. Sanitization is the process of removing sensitive information from a document or other message or sometimes encrypting it, so that the document may be distributed to a broader audience. When the intent is secrecy protection, such as in dealing with classified information, sanitization attempts to reduce the documents classification level, possibly yielding an unclassified document. When the intent is privacy protection, it is often called data anonymization. Originally, the term sanitization was applied to printed documents it has since been extended to apply to computer media and the problem of data remanence as well. Redaction in its sanitization sense as distinguished from its other editing sense is the blacking out or deletion of text in a document, or the result of such an effort. It is intended to allow the selective disclosure of information in a document while keeping other parts of the document secret. Typically the result is a document that is suitable for publication or for dissemination to others than the intended audience of the original document. For example, when a document is subpoenaed in a court case, information not specifically relevant to the case at hand is often redacted.  Government secrecyeditIn the context of government documents, redaction also called sanitization generally refers more specifically to the process of removing sensitive or classified information from a document prior to its publication, during declassification. Secure document redaction techniquesedit. A US government document that has been redacted prior to release. The traditional technique of redacting confidential material from a paper document before its public release involves overwriting portions of text with a wide black pen, followed by photocopying the resultthe obscured text may be recoverable from the original.
Government secrecyeditIn the context of government documents, redaction also called sanitization generally refers more specifically to the process of removing sensitive or classified information from a document prior to its publication, during declassification. Secure document redaction techniquesedit. A US government document that has been redacted prior to release. The traditional technique of redacting confidential material from a paper document before its public release involves overwriting portions of text with a wide black pen, followed by photocopying the resultthe obscured text may be recoverable from the original.  Alternatively opaque cover up tape or redaction tape, opaque, removable adhesive tape in various widths, may be applied before photocopying. This is a simple process with only minor security risks. For example, if the black pen or tape is not wide enough, careful examination of the resulting photocopy may still reveal partial information about the text, such as the difference between short and tall letters. The exact length of the removed text also remains recognizable, which may help in guessing plausible wordings for shorter redacted sections. Where computer generated proportional fonts were used, even more information can leak out of the redacted section in the form of the exact position of nearby visible characters. The UK National Archives published a document, Redaction Toolkit, Guidelines for the Editing of Exempt Information from Documents Prior to Release, to provide guidance on the editing of exempt material from information held by public bodies. Secure redacting is a far more complicated problem with computer files.
Alternatively opaque cover up tape or redaction tape, opaque, removable adhesive tape in various widths, may be applied before photocopying. This is a simple process with only minor security risks. For example, if the black pen or tape is not wide enough, careful examination of the resulting photocopy may still reveal partial information about the text, such as the difference between short and tall letters. The exact length of the removed text also remains recognizable, which may help in guessing plausible wordings for shorter redacted sections. Where computer generated proportional fonts were used, even more information can leak out of the redacted section in the form of the exact position of nearby visible characters. The UK National Archives published a document, Redaction Toolkit, Guidelines for the Editing of Exempt Information from Documents Prior to Release, to provide guidance on the editing of exempt material from information held by public bodies. Secure redacting is a far more complicated problem with computer files.  Word processing formats may save a revision history of the edited text that still contains the redacted text. In some file formats, unused portions of memory are saved that may still contain fragments of previous versions of the text. Where text is redacted, in Portable Document Format PDF or word processor formats, by overlaying graphical elements usually black rectangles over text, the original text remains in the file and can be uncovered by simply deleting the overlaying graphics. Effective redaction of electronic documents requires the removal of all relevant text or image data from the document file. This either requires a very detailed understanding of the internal operation of the document processing software and file formats used, which most computer users lack, or software tools designed for sanitizing electronic documents see external links below. Redaction usually requires a marking of the redacted area with the reason that the content is being restricted. Yesterday, I received a note via email from a consultant who asked Why did Adobe eliminate the Previous Page and Next Page buttons from Acrobat X The Malcolm Baldrige National Quality Improvement Act of 1987 PDFPublic Law 100107The Malcolm Baldrige National Quality Award was created by Public Law 100107. US government documents being released under the Freedom of Information Act are marked with exemption codes that denote the reason why the content has been withheld. The US National Security Agency NSA published a guidance document which provides instructions for redacting PDF files. 1Printed matteredit. A page of a classified document that has been sanitized for public release. This is page 1. 3 of a U. S. National Security Agency report 1 on the USS Liberty incident, which was declassified and released to the public in July 2. Classified information has been blocked out so that only the unclassified information is visible. Notations with leader lines at top and bottom cite statutory authority for not declassifying certain sections. Click on the image to enlarge. Printed documents which contain classified or sensitive information frequently contain a great deal of information which is less sensitive. There may be a need to release the less sensitive portions to uncleared personnel. Shop for adobe acrobat pro at Best Buy. Find low everyday prices and buy online for delivery or instore pickup. The Acrolaw Blog is a resource for lawyers, law firms, paralegals, legal IT pros and anyone interested in the use of Acrobat in the legal community. Rick Borstein. View and Download Adobe Photoshop CS6 user manual online. Photoshop CS6 Software pdf manual download. Here is a little secret It is very easy to duplicate a page in Adobe Acrobat and most Acrobat users dont know about this trick. Open up Acrobat and display the. View and Download Adobe 65030089 Robohelp PC using manual online. User Manual. 65030089 Robohelp PC Software pdf manual download. Tech and Science topics phones, computers, gadgets, and the Internet, astronomy earth science, climate weather, environment green living and much more. Click here for the Valkyrie FAQ Page Valkyrie Maintenance Guide by Carl Kulow send commentscorrections to kulowcindiana. edu. ISBN F61520CC First Edition. Learn about how Adobe Scout works and how to use it. The printed document will consequently be sanitized to obscure or remove the sensitive information. Maps have also been redacted for the same reason, with highly sensitive areas covered with a slip of white paper. In some cases, sanitizing a classified document removes enough information to reduce the classification from a higher level to a lower one. For example, raw intelligence reports may contain highly classified information such as the identities of spies, that is removed before the reports are distributed outside the intelligence agency the initial report may be classified as Top Secret while the sanitized report may be classified as Secret. In other cases, like the NSA report on the USS Liberty incident right, the report may be sanitized to remove all sensitive data, so that the report may be released to the general public. As is seen in the USS Liberty report, paper documents are generally sanitized by covering the classified and sensitive portions and then photocopying the document, resulting in a sanitized document suitable for distribution. Computer media and fileseditComputer electronic or digital documents are more difficult to sanitize. In many cases, when information in an information system is modified or erased, some or all of the data remains in storage. This may be an accident of design, where the underlying storage mechanism disk, RAM, etc. still allows information to be read, despite its nominal erasure. The general term for this problem is data remanence. In some contexts notably the US NSA, Do. D, and related organizations, sanitization typically refers to countering the data remanence problem redaction is used in the sense of this article. However, the retention may be a deliberate feature, in the form of an undo buffer, revision history, trash can, backups, or the like. For example, word processing programs like Microsoft Word will sometimes be used to edit out the sensitive information. Unfortunately, these products do not always show the user all of the information stored in a file, so it is possible that a file may still contain sensitive information. In other cases, inexperienced users use ineffective methods which fail to sanitize the document. Metadata removal tools are designed to effectively sanitize documents by removing potentially sensitive information. In May 2. 00. 5 the US military published a report on the death of Nicola Calipari, an Italian secret agent, at a US military checkpoint in Iraq. It Still Works Giving Old Tech a New Life. Software How to Run Trend Micro in Safe Mode Trend Micro, an antivirus provider that offers program and online based virus scanning solutions, is a great way to get rid of malicious software. By Margaret Worthington.
Word processing formats may save a revision history of the edited text that still contains the redacted text. In some file formats, unused portions of memory are saved that may still contain fragments of previous versions of the text. Where text is redacted, in Portable Document Format PDF or word processor formats, by overlaying graphical elements usually black rectangles over text, the original text remains in the file and can be uncovered by simply deleting the overlaying graphics. Effective redaction of electronic documents requires the removal of all relevant text or image data from the document file. This either requires a very detailed understanding of the internal operation of the document processing software and file formats used, which most computer users lack, or software tools designed for sanitizing electronic documents see external links below. Redaction usually requires a marking of the redacted area with the reason that the content is being restricted. Yesterday, I received a note via email from a consultant who asked Why did Adobe eliminate the Previous Page and Next Page buttons from Acrobat X The Malcolm Baldrige National Quality Improvement Act of 1987 PDFPublic Law 100107The Malcolm Baldrige National Quality Award was created by Public Law 100107. US government documents being released under the Freedom of Information Act are marked with exemption codes that denote the reason why the content has been withheld. The US National Security Agency NSA published a guidance document which provides instructions for redacting PDF files. 1Printed matteredit. A page of a classified document that has been sanitized for public release. This is page 1. 3 of a U. S. National Security Agency report 1 on the USS Liberty incident, which was declassified and released to the public in July 2. Classified information has been blocked out so that only the unclassified information is visible. Notations with leader lines at top and bottom cite statutory authority for not declassifying certain sections. Click on the image to enlarge. Printed documents which contain classified or sensitive information frequently contain a great deal of information which is less sensitive. There may be a need to release the less sensitive portions to uncleared personnel. Shop for adobe acrobat pro at Best Buy. Find low everyday prices and buy online for delivery or instore pickup. The Acrolaw Blog is a resource for lawyers, law firms, paralegals, legal IT pros and anyone interested in the use of Acrobat in the legal community. Rick Borstein. View and Download Adobe Photoshop CS6 user manual online. Photoshop CS6 Software pdf manual download. Here is a little secret It is very easy to duplicate a page in Adobe Acrobat and most Acrobat users dont know about this trick. Open up Acrobat and display the. View and Download Adobe 65030089 Robohelp PC using manual online. User Manual. 65030089 Robohelp PC Software pdf manual download. Tech and Science topics phones, computers, gadgets, and the Internet, astronomy earth science, climate weather, environment green living and much more. Click here for the Valkyrie FAQ Page Valkyrie Maintenance Guide by Carl Kulow send commentscorrections to kulowcindiana. edu. ISBN F61520CC First Edition. Learn about how Adobe Scout works and how to use it. The printed document will consequently be sanitized to obscure or remove the sensitive information. Maps have also been redacted for the same reason, with highly sensitive areas covered with a slip of white paper. In some cases, sanitizing a classified document removes enough information to reduce the classification from a higher level to a lower one. For example, raw intelligence reports may contain highly classified information such as the identities of spies, that is removed before the reports are distributed outside the intelligence agency the initial report may be classified as Top Secret while the sanitized report may be classified as Secret. In other cases, like the NSA report on the USS Liberty incident right, the report may be sanitized to remove all sensitive data, so that the report may be released to the general public. As is seen in the USS Liberty report, paper documents are generally sanitized by covering the classified and sensitive portions and then photocopying the document, resulting in a sanitized document suitable for distribution. Computer media and fileseditComputer electronic or digital documents are more difficult to sanitize. In many cases, when information in an information system is modified or erased, some or all of the data remains in storage. This may be an accident of design, where the underlying storage mechanism disk, RAM, etc. still allows information to be read, despite its nominal erasure. The general term for this problem is data remanence. In some contexts notably the US NSA, Do. D, and related organizations, sanitization typically refers to countering the data remanence problem redaction is used in the sense of this article. However, the retention may be a deliberate feature, in the form of an undo buffer, revision history, trash can, backups, or the like. For example, word processing programs like Microsoft Word will sometimes be used to edit out the sensitive information. Unfortunately, these products do not always show the user all of the information stored in a file, so it is possible that a file may still contain sensitive information. In other cases, inexperienced users use ineffective methods which fail to sanitize the document. Metadata removal tools are designed to effectively sanitize documents by removing potentially sensitive information. In May 2. 00. 5 the US military published a report on the death of Nicola Calipari, an Italian secret agent, at a US military checkpoint in Iraq. It Still Works Giving Old Tech a New Life. Software How to Run Trend Micro in Safe Mode Trend Micro, an antivirus provider that offers program and online based virus scanning solutions, is a great way to get rid of malicious software. By Margaret Worthington.
Top Pages
- Sam Crescent Free Ebook Download
- Eset Smart Security 6 Beta Cracked Minecraft
- Windows Is Uninstalling This Device Code 212
- Vista Pacifica San Clemente Reviews Of Doctors
- Install Oracle Express Linux Rpm Uninstall
- Cara Menghapus File Yang Tidak Bisa Dihapus Dengan Software Download
- Mcafee Epo Command Line Install Python